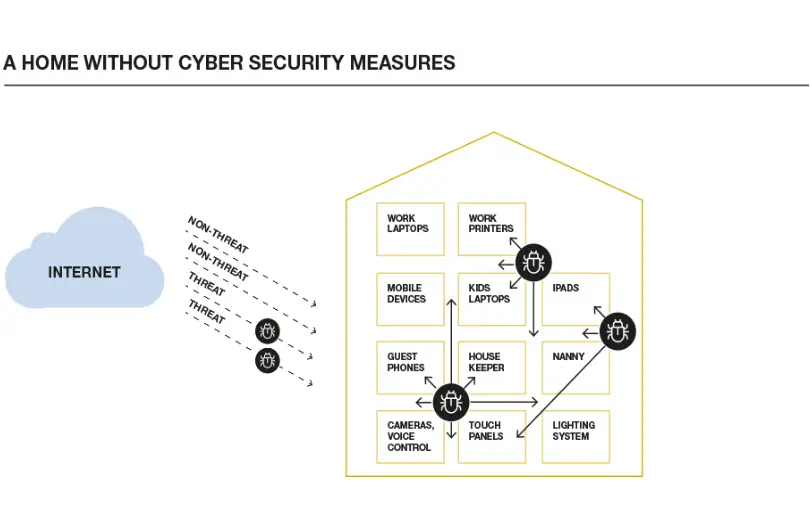
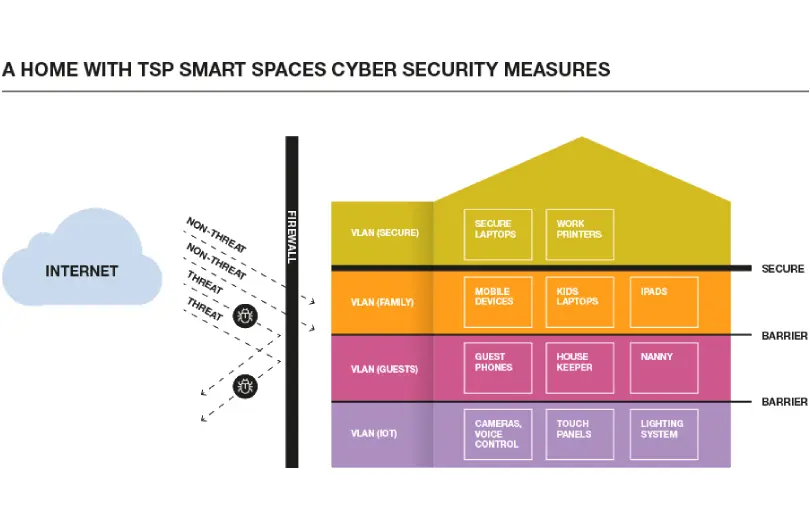
During 2020, the home became not just the hub of personal life but of work life as well. As our daily routines were disrupted, we found our homes turned into full-time schools, cinemas, playgrounds, and workplaces. As the weeks turned into months, we realized that this overnight shift increased risk for our clients, and we needed to figure out how good their home cybersecurity was, to make sure that all of their work and personal lives were protected from cyber attack.
The home network has frequently been ignored from a cybersecurity standpoint. It’s considered by most employers as a “zero trust” network – just like public WiFi in an airport. But it’s even worse than public Wi-Fi: if a hacker breaks into your home network, they now have 24/7 access to try to break into your personal and work computers. So we turned to the cybersecurity audit team at Tech Superpowers (TSP) to help us create a solution – one that provides a cyber risk assessment of your home at a reasonable price.
The result is the world’s/region’s/area’s first Cybersecurity Audit for Home product, which focuses on homes of executives and high net worth individuals to ensure that cyber threats are properly evaluated with the rapid shift of working from home.
When we go into an existing smart home to determine how safe a customer’s home is, we look at three primary elements:
(1) their network stack
(2) existing documentation of their smart home technologies
(3) any devices which give outside access to the network – by permission or, worse yet, without permission.
Below, we’ll walk you through why these three primary areas matter.
Why does cybersecurity matter in a smart home?
For those of us living in large homes, even in the safest neighborhoods, we’ve been used to paying for dependable alarm systems and security companies who monitor our alarms and can respond to break-ins. What are we really protecting in our home? From the standpoint of physical security: maybe some expensive electronics, jewelry, and our personal safety and protection. From a digital security standpoint, the stakes are even higher.
Losing access to bank accounts and financial information can easily cost you tens of thousands of dollars, if not more. In fact, at Tech Superpowers, we’ve seen successful cybersecurity fraud schemes that have netted criminals over $800,000. And while few worry about personal safety threats over the internet, identity theft often has ongoing consequences to the victim.
So, why do few people pay for cybersecurity audits for the home?
First, there’s never been a company that provides cybersecurity audits dedicated for today’s homes. TSP is one of the first companies to provide a dedicated service for residential homes.
Second, cyber threats don’t feel that real, especially for home users. People don’t report cyber attack damages to their local police as they do with break-ins, so you don’t ever hear of them. But if you talk to someone in cybersecurity insurance or the FBI, who is responsible for interstate wire fraud, the numbers are real. According to Cybersecurity Ventures, damages are estimated to hit 6 trillion dollars in 2021. This represents more losses than caused by drug trafficking or any other major type of crime.
Third, the amount of high-transactional business that happens on home networks has traditionally been a small fraction of what might be happening on business networks, so most people just figure that hackers will not target the usual smart home. That changed in 2020, as everyone started to work from home and the amount of critical transactional business shifted dramatically to being mostly from home vs at the office.
54% of IT professionals think that remote workers pose a greater security risk than on-site workers – OpenVPN
Even with an alarm system, seldom do the police catch a robbery in progress. But their services are still essential. Why? Because they work as a deterrent and they provide some protection in case of a worst-case that will likely never happen. We need to start thinking about cybersecurity protection for home networks in the same way: as a deterrent and protection against the worst case.
The 3 questions we ask when performing a smart home cybersecurity audit
The first thing that we look at in a home network is the current network stack. The first generation of smart home dealers came from the world of HiFi – and they didn’t know much about networks. Many of them still don’t – and we know that because we frequently see consumer-grade equipment put in for a $500K smart home system.
As most people found out during the first wave of the pandemic, what matters most isn’t your six-figure speakers but your Wi-Fi and core network. If those aren’t functioning correctly, you have unhappy work-from-home parents and frustrated remote-learning kids. Similarly, in the world of cybersecurity, what keeps your home running is the core of the network.
When we perform a smart home cybersecurity audit, we ask the following 3 questions.
How much did cybersecurity matter to your smart home integrator?
First, we look at the brands which were installed. If your integrator used Linksys or D-link, they opened you up for hacks redirecting you to Coronovirus misinformation. If they used any of the 100,000 Zyxel products out there, they opened you up to backdoors hackers are using every day to penetrate networks.
If you have systems by Ruckus, Araknis, or Ubiquiti, you’re in better hands. These are more specialist brands that are generally more secure than consumer brands sold a dime a dozen. But that still doesn’t mean that you’re fully secure. In 2019, a security researcher found three critical vulnerabilities on Ruckus wireless routers that could be used to gain “root” privileges on the router and allowed the attacker unlimited access to the device and the entire network. While Ruckus quickly fixed the vulnerabilities, customers were required to update their devices themselves, a task that may prove too technical for the average user.
TSP recommends networks by Cisco Meraki for our smart homes. Not only is Meraki backed by enterprise security heavyweight Cisco, but it’s also used by some of the most cyber secure organizations in the world, including MIT, Montefiore Hospital, and our client, Accel. Meraki routers include AMP (advanced malware protection) for rapid detection of new and emerging threats. This does more than just prevent users from downloading malware – it “provides comprehensive security before, during, and after a malware attack.”*
*Source – https://meraki.cisco.com/solutions/amp
We install only the best network protection for our customers. After years of utilizing Meraki for our routers, we feel secure in the protection their routers and Cisco provides for our customers and their homes.
Was your home network set up with network documentation?
Next, we look at the client’s network documentation to see how well the network has been planned and implemented.
I know that for most of us, especially those who have put together our own home networks, the idea of planning out a network seems silly. Don’t you just plug things into the WiFi router and turn them on?
While that might be the case for the simplest of networks, the types of houses we work on have different technology scale. In one of our projects, a 3000 sq-ft home in the Back Bay of Boston, there were over 300 connected devices, with over 122 operating on the core network at the same time. Connected devices in a home are all part of the Internet of Things (IoT) and can pose a serious security risk to your home’s network unless installed correctly. According to NETSCOUT’s Threat Intelligence Report in 2018, it takes the average hacker only 5 minutes to hack an IoT device. For a large scale network to be secure, you have to design and plan for scale and growth.
If your smart home doesn’t have any network documentation, then it’s probably not built with cybersecurity in mind. Properly designed networks have multiple “VLANs” (Virtual Local Area Networks) to help protect different classes of devices. These enable groups of devices connected to your network to be partitioned into separate virtual networks as an added layer of network security. So your critical work devices live on a different network from your IoT devices, which are much more vulnerable to attack.
Putting together a secure network requires thought and planning, and when we see a network with a lack of plan, it’s our job to make sure that everything is fixed in a way where all of network traffic is segmented properly and all WiFi access is secure.
What outside devices have access to your network?
Finally, we take a look at any devices that might have access to your network outside of your home. These could be PCs installed with remote access software for maintenance purposes or cloud-based systems IoT devices that can be accessed remotely from an app. Any external device that gains access to your home network poses a security risk and provides another access point for hackers to target your system.
In a recent home cybersecurity audit we performed, we found that a past vendor retained access to the home’s entire network with a single username and password, shared amongst their entire company. While this luckily did not lead to a successful attack on their systems, it did pose a major security risk to their home. Access given to contractors and vendors often pose the largest security for your home and offer an easy access point for hackers. This was the case in Target’s 2013 data breach, where hackers gained access to 40 million credit card numbers in one of the most significant data breaches in history. In the Target data breach, hackers stole credentials from a third-party HVAC vendor to break into its billing platform.
By checking what external devices or people have access to your network and either removing or modifying network permissions for each, we can mitigate the risks to your network posed by these outside sources.
Ensure your home’s cybersecurity
With the Covid-19 pandemic, more and more of us are working from home, resulting in our home networks becoming not just a hub for our personal information but our crucial business information as well. This bypasses the tens of thousands of dollars most businesses put in place with enterprise firewalls and leaves business data in the hands of your home network. Our process is to begin to look at homes as places of business and apply the same rigorous standards to your home network as we do any business network.
On the go? Check out these tips for staying safe while on public Wi-Fi.
Is your home network well protected from a potential cyber attack? Contact us to schedule your smart home cybersecurity audit!